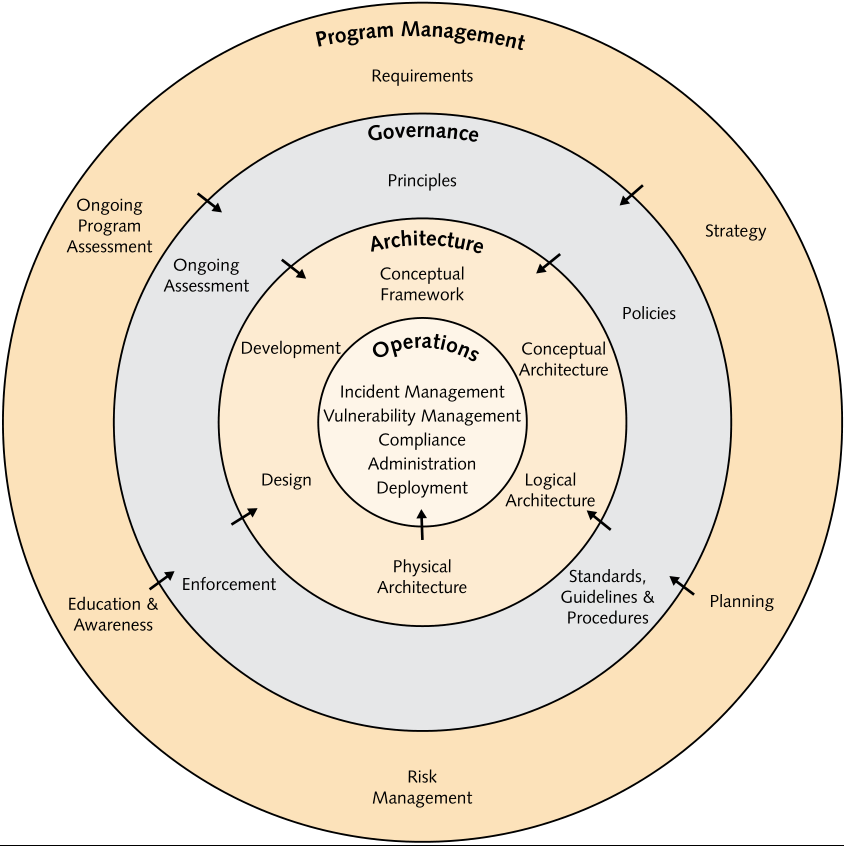
Figure 1 - Source: O-ESA G112
TRISIS, otherwise known as TRITON and HATMAN is a piece of malware that targets industrial control systems (ICS) and was discovered in late 2017. This malware was written specifically to target the Schneider Electric Triconex safety instrumented system (SIS), specifically the Triconex 3008 processor module.[1] As sensational as some articles might be, TRISIS did nothing, an error in the code prevented successful execution which would have disabled the SIS and led to operations halting or a complete disaster.
The real impact of TRISIS is not the physical damage and destruction that could have occurred, but the resulting code being modified and targeted at different SIS and a whole new world of attacks against industrial control systems (ICS) worldwide. TRISIS may be considered a proof of concept, it proved quite spectacularly that not only are ICS vulnerable to attack, but that the attackers were persistent in the environment for more than 12 months without being detected.
TRISIS was most definitely not the first malware to target industrial control systems, not only has there been predecessors specifically targeted at destroying the uranium enrichment process but common ransomware has infected human machine interfaces (HMI) causing loss of monitoring and control, and ultimately blackouts across entire countries.
TRISIS is said to be a game changer[1], not only because of the successful persistent threat, but also the specific targeting of SIS and the capability to potentially bring these life saving devices down.
Although the world has experienced that connecting devices and convergence without performing due diligence a generally bad idea and targets are primarily opportunistic (exceptions do exist, of course), not connecting devices does not make you safe. Air gaps can be breached, sometimes very easily by carrying a USB key, sometimes they're breached because of poor documentation, and sometimes they are breached through highly sophisticated attacks using voltage changes to transfer data between devices[2].
Organisations maintaining ICS need to bring themselves into the 21st century of technology, which is a wild statement, but necessary. When Information Technology (IT) and Operational Technology (OT) convergence has found its way into the business strategy we find that although IT has good cybersecurity controls implemented, OT is very lacking both in the capability to implement and the capacity to support added controls. OT is a broad statement covering ICS, SCADA, PLC's, SIS, Building Management Systems (BMS), sensor arrays, and everything else not associated with traditional IT. OT environments consist of devices that often required 100% uptime, devices are not rebooted for fear of never turning back on, further, they run with at high utilisation / low capacity limiting the ability to implement cybersecurity controls without a major uplift.
Stepping into the 21st century for OT does not need to be daunting and needs to take a structured approach to business strategy, goals and aligning the OT environment with these. A lot of principles from IT are still very applicable in OT, there is no need to rebuild the process for implementing cybersecurity in your OT environment. The enterprise security model in figure 1 from the Open Enterprise Security Architecture (O-ESA) by the Open Group provides a well formed and structured approach to developing an enterprise security architecture. Utilising the same governance approach for enterprise IT as taken for OT provides added efficiencies and understanding of processes, policy and assists in developing an aligned approach to cybersecurity for the organisation as a whole. Ultimately, leveraging this framework helps break down the silo's IT and OT work in, allowing incompatible teams to work together, enabling IT and OT convergence and further enhancing the capability and capacity to align with business strategy and achieve business goals.

The key factor in developing a successful organisational security architecture is understanding that, technically, the approach to implementation is different, as different as French cuisine is to American Hotdogs. The same concepts apply, primarily that of implementing a zone architecture and ensuring the functionally independent devices are isolated from each other. In IT, the focus is primarily on a simple three tier architecture consisting of interfaces, logic, and storage, whereas OT and focuses on isolation of based on function, such as smart grids and their zones, transmission, distribution, and generation of power.
With all zone model approaches, identifying system criticality, is well, critical. A critical system warrants additional controls to ensure it is resilient, redundant, and protected from high threat attacks. Figure 2 shows a detailed security zone architecture, with consideration that each box is representative of multiple sub-zones, which is easily adapted to OT environments as seen in Figure 3, which provides each zone logical and physical separation from each other.
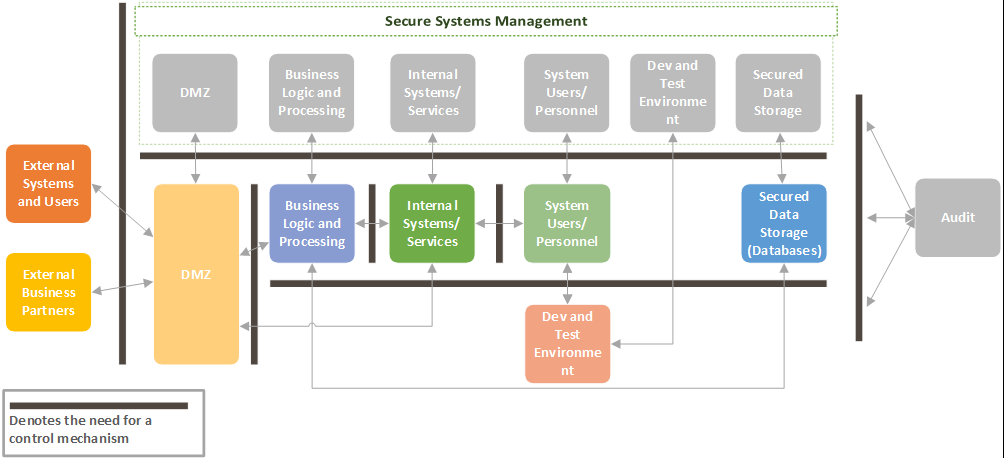
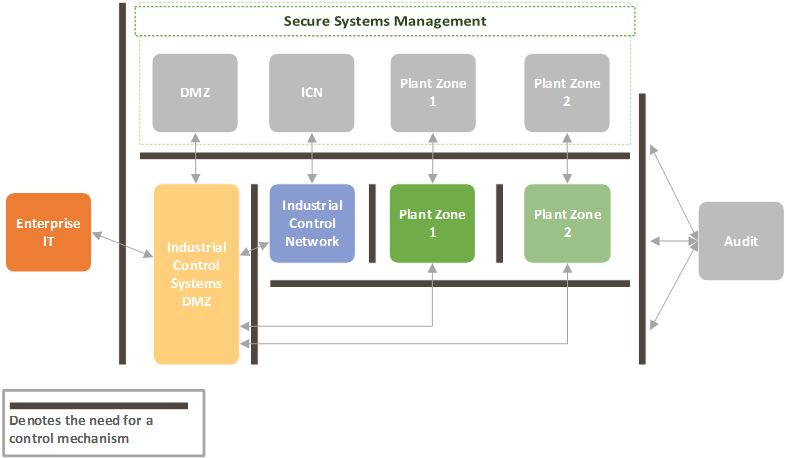
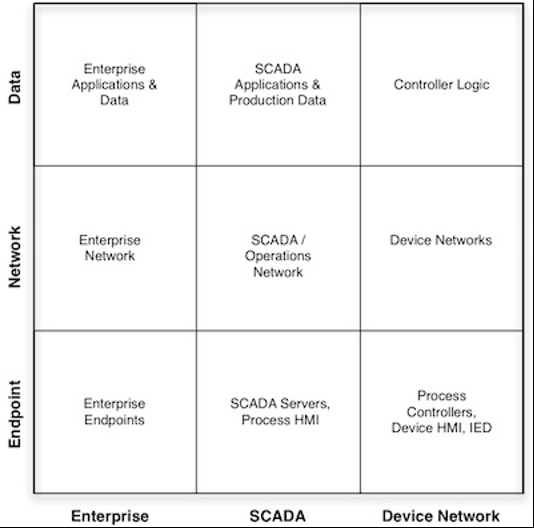
Although Enterprise IT can have an all-in approach to cybersecurity (all controls all, all monitoring, all seeing, all preventing), OT environments have an added level of complexity - their environments consist of low level devices such as pumps, motors, and actuators, logic controllers, including SIS, to data historians, HMI's and workstations. To capture these diverse systems, the McAfee 3x3 security model should be considered, each column reflects business, SCADA, and plant components and each row represents data, network, and endpoint systems. This model, when applied to specific systems, such as the power generation function of a plant can help classify components utilised and enables an educated approach to implementing cybersecurity controls[4], the matrix can be seen in figure 4.
IT is seen as a business enabler, without IT most businesses cannot function let alone exist (what is Google, if not for the Internet). OT, too, is an enabler, it enables us to live our lives, safely, with electricity, water, gas… the Internet. Cybersecurity is often still seen as that annoying little brother, running around poking faults at everything and hindering the business. Cybersecurity is a business enabler, it enables business to operate safely in hostile environments, it enables safe and protected convergence of IT and OT, it protects the business from others and from itself. Businesses need to engage from the top down, delivering strategy, but also bottom up and ensuring that technically the strategy is achievable. Integrate a cyclic process, even of the simplest nature, plan-do-check-act, to foster the continual growth, learning and correction required to bring OT security into the 21st century.