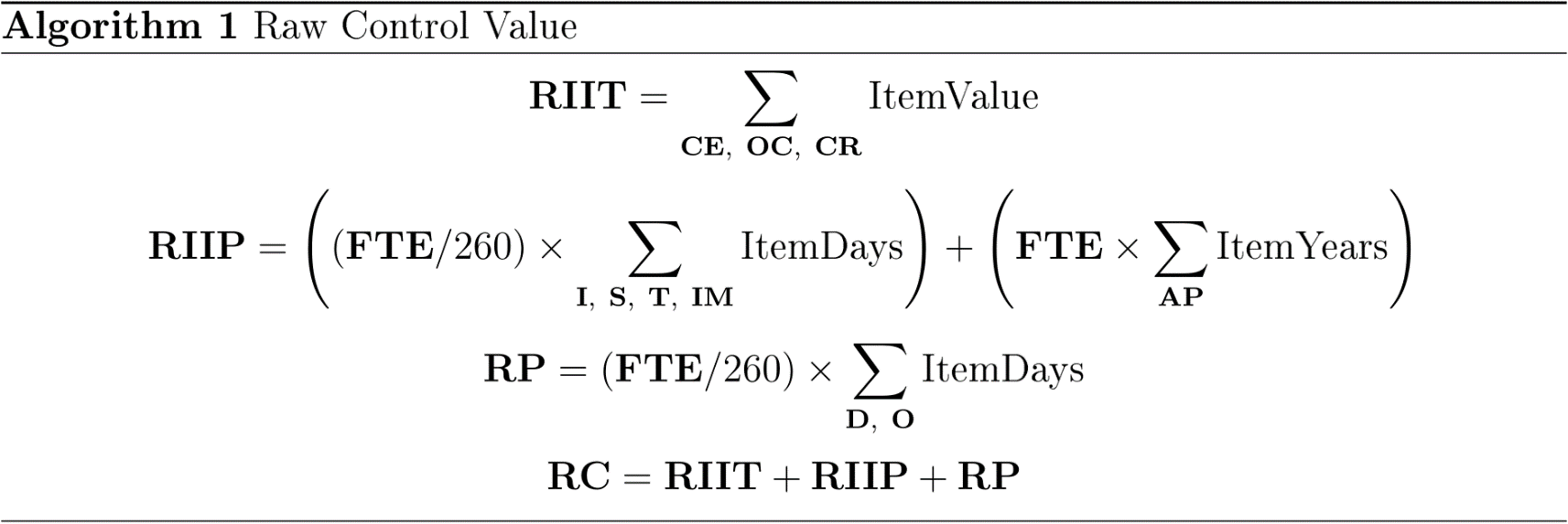
I once wrote a dry, boring, and interesting (to me) essay for University in an attempt to determine a valid method for calculating the cost of information security controls based on a number of various factors. I've used the calculations in simulations and in real-world scenarios with a decent amount of success to validate that in the estimation and prioritisation game, this calculation method can be useful.
What is presented below is the essence of the overly long and dry essay.
There exists no uniform set of information security controls that can be applied universally. Full stop.
Information security standards are an attempt to address the lack of security in an organisation, yet every standard is accompanied with commentary along the lines of "being compliant/certified to standard XYZ does not mean you are secure." Security standards are a starting ground for implementing information security controls, implementing all of the controls do not make you secure… in fact, doing so would probably result in the opposite, along with making a bunch of vendors extremely happy.
Information Security standards provide guidance and recommendations to organisations on how they should improve their level of security and how to value their assets appropriately. The problem is that many standards are massive undertakings of work that require significant effort and knowledge to implement.
Effort is a problem, even with implementation of controls in a standard, there is no assurance that the controls implemented will perform as expected, if they are required, and even if they provide any benefit to the organisation. Simply, does the control reduce (or contribute to reduction) risk to an acceptable tolerable amount, or at least enable the business to perform.
Selecting a standard to implement con be an issue itself. How do you determine which is appropriate for your business? Well, simple, what are you legally and contractually obliged and required to adhere to? If you're a merchant, PCI-DSS is probably your cup of tea. If you're a government agency, your government will most certainly have a standard you must adhere to. Which leads us to the cost...
Implementing security controls can be an onerous task and if done without structure can easily result in inadequate and ineffective security controls being deployed. To provide a level of structure and guidance with implementation of information security, a number of standards, frameworks, regulations, guidelines, and benchmarks have been developed.
This raises the primary question: what is the value of the technical controls suggested by the standards?
A review of a group of information security standards has resulted in a catalogue of common controls that should be implemented, of which, the value of implementing needs to be identified. This requires identification of the coverage, effectiveness, cost, penalties, loss for non-compliance, relevance, type, and overhead of the control.
To effectively assess the value of a control, we should define some principles. So here are seven I came up with.
| 1. | Information security is integral to organisational strategy |
| 2. | Information security impacts all aspects of the organisation |
| 3. | Enterprise risk management defines information security requirements. |
| 4. | Information Security Accountabilities Should be De?ned and Acknowledged |
| 5. | Information Security Must Consider Internal and External Stakeholders |
| 6. | Information Security Requires Understanding and Commitment |
| 7. | Information Security Requires Continual Improvement |
Some research uncovered numerous articles being reviewed and analysed for similarities between the goal of my University paper and any previous works. What I came up with was a bunch of papers with a focus on the applicability of technical security controls and their effectiveness in reducing risk or providing an analysis on the similarities between implementation of standards.
There is very little focus on the cost and potential overall value of implementation of information security standards. One method, PROMETHEE, was proposed which takes a similar approach to what I describe below, however, it focuses within the realm of applicability of a technical control to address risk.
These items define the columns used in the magical spreadsheet… which you can contact me to obtain. Or, use the algorithms below to create one!
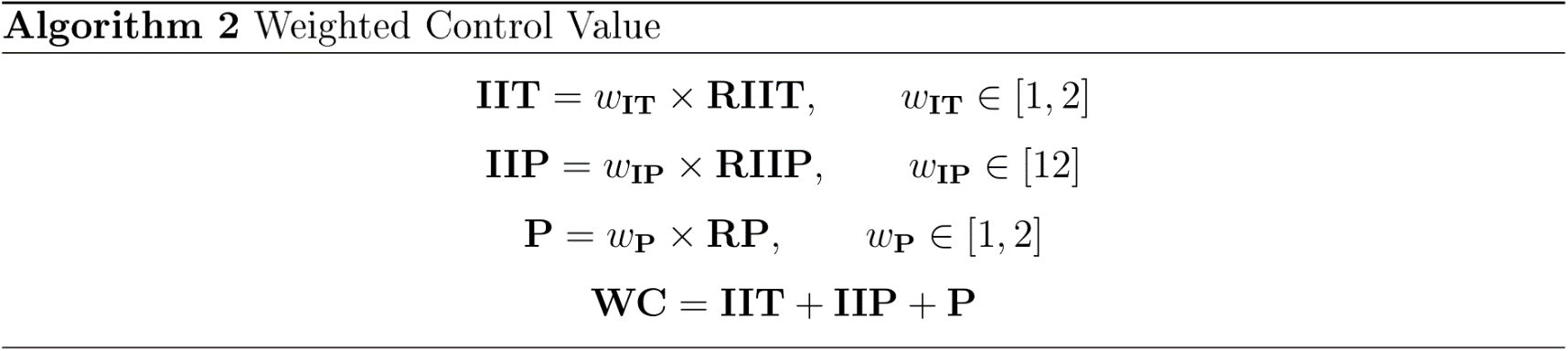
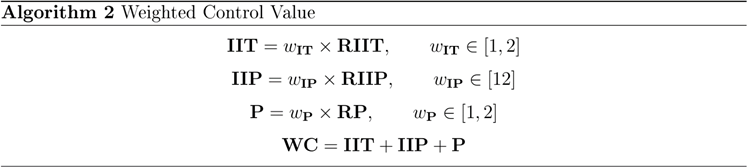
| WC: | Weighted Cost | The sum of the criteria defined below multiplied against the weighting value. This value represents what is considered value or cost of the solution is for an organisation. This can be considered the value in which to assign to an information security budget. |
|---|---|---|
| RC: | Raw Cost | The sum of all costs associated with the technical control without considering any weighting or variations. This is the cost that closest resembles the actual financial burden of the technical control. |
| CO: | Comparison value | A percentage value representing the difference between the weighted cost and raw cost. A value of 100% represents that the weighted cost is identical to the raw cost. If this value is higher than 100%, it represents that the inherent worth of the control is greater than the financial burden it imposes. |
| W: | Weighting | This is a subjective value assigned by the entity operating the calculations, where the importance of the category is higher, this value should be closer to 2, and if it is lower, this should be assigned a value closer to 1. These values must represent the importance of the category to the entity and should align with the organisations information security strategy. |
| FTE: | Full Time Equivalent | Assigned a value annual salary. |
| Control Name: | Name of the technical control. | |
| CE: | Capital Expenditure ($) | Initial cost associated with purchasing the technical security control. This may be a dollar value equal to or greater than zero, where a zero value is due to the required software/application being included in existing systems or infrastructure. |
| OC: | Ongoing Cost ($/year) | Operational costs associated with the maintenance and support of the technical control. This will primarily be the value of ongoing vendor support where applicable. |
| CR: | Cost Reduced by Existing Systems / Infrastructure (Reduction $) | If an existing system exists within the infrastructure that may assist in reducing the overall implementation cost the value of the reduction is to be recorded here. |
| AH: | Additional Hardware Required ($) | Value of additional hardware if required beyond any inclusion of the capital expenditure. For instance, where a physical appliance is being purchased, the physical system cost is incorporated into the technical control capital expenditure. |
| I: | Implementation (Days) | The amount of time required to implement the technical control from conception through to completion. |
| S: | Support (Days/year) | The amount of ongoing time that needs to be allocated to support the technical control. |
| AP: | Additional Personnel Required (FTE). | |
| T: | Training (Days/year) | The amount of training required to ensure personnel are capable of operating and maintaining the technical control. |
| IM: | Impact (Days/year) | This is the impact upon operational services the implementation and operation of the technical control may have. The time value is to represent the amount of time spent due to apparent issues. |
| D: | Defining (Days/year) | The number of FTE's required to define and write the processes related to the operation of the technicalcontrol. |
| O: | Operating (Days/year) | The number of FTE's required to operate and implement the processes defined, this can be seen as internal support. |
| S: | Specialist Required (Y/N) | Is a specialist required for the implementation of the technical control. |
| CD: | Commonly Deployed / Provided (Y/N) | |
| IS: | Improve Security Posture (Y/N) | |
| PA: | Potential Alternatives (List) | List the number of alternative technical implementations that are similar to the proposed control. |
| PR: | Provides (Reference) | List the references from the identified security standards to provide a direct mapping between this control and what it achieves. |
| AR: | Addresses Requirement (Y/N) | Clearly state if this technical control fully addresses the requirement of the security standard or the organisation. |
These algorithms are the underlying magic to implement all the magic above into something that should give you strong guidance on whether a control is suitable for your organisation.
Further, this is not assessing the control against risk, but
primarily against time and effort. Many controls can be
implemented to reduce risk, this algorithm should help you
determine which is the best.
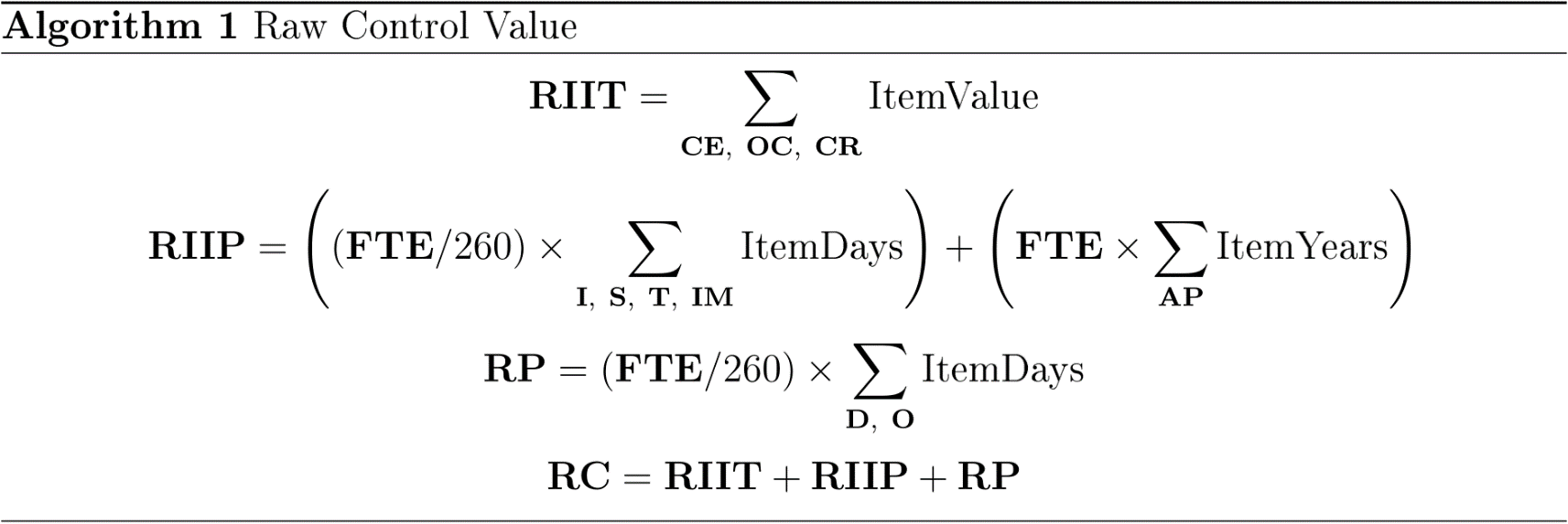
If you're interested in further details, contact me.